Generative AI is rapidly gaining mainstream status, likely best represented by Chat GPT. Which, in early 2023, became the fastest growing app in the history of web applications reaching one million users in just five days (in comparison Instagram took 2.5 years).
While there are numerous legitimate use cases for this technology, the adoption of Generative AI brings new challenges especially in terms of security. In this blog post we'll explore the rise of Generative AI, how it impacts phishing attacks and strategies to enhance fraud prevention in the face of these evolving threats.
- How AI is changing the fraud landscape
- How to counter AI-driven phishing attacks
- The fraud prevention toolkit
How generative AI lowers the barrier to entry for criminals
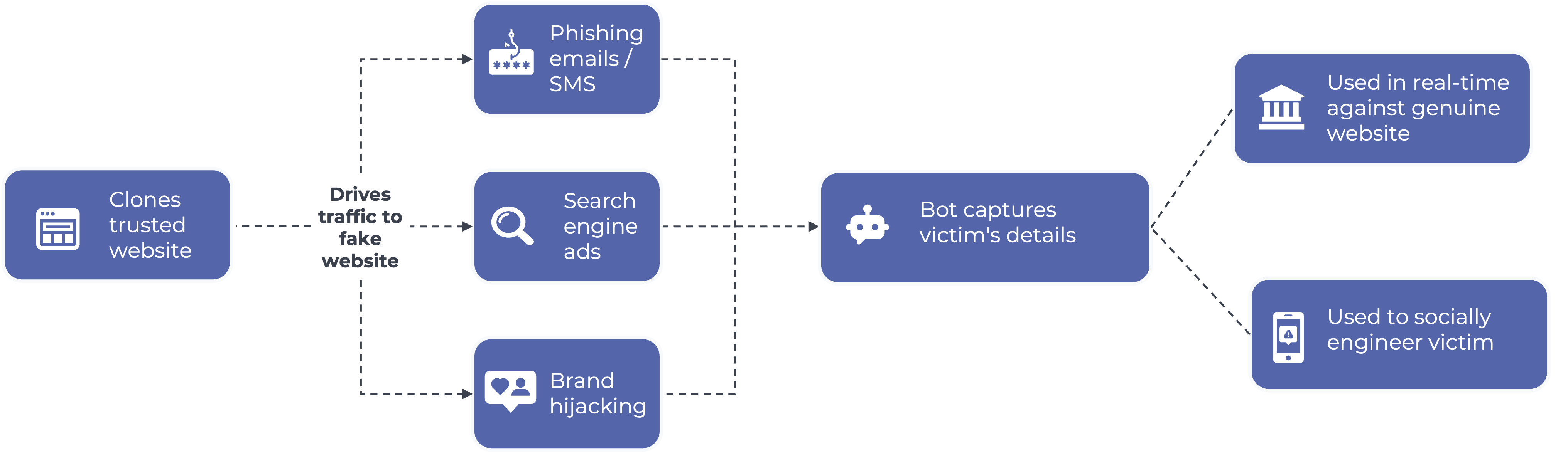
Generative AI has enabled cybercriminals to conduct fraud campaigns that are more scalable and effective. This can be seen from the recent explosion in phishing sites targeting all sectors from banking and insurance, to government & e-commerce. Some vendors are reporting that a new phishing site is created on the internet every 11 seconds.
While phishing attacks still follow the familiar pattern of cybercriminals creating convincing messages and websites to deceive users into revealing sensitive information, Generative AI is making this significantly easier by lowering the barrier to entry for fraudsters by:
- reducing required skills & resources need to conduct an attack
- reducing time allowing fraud to be executed at a quicker pace
- reducing cost across headcount and applications
- increasing the total addressable market (having a multi-national reach and run concurrent scams)
This is made possible as Generative AI removes the traditional limitations around committing fraud by augmenting a fraudster’s capabilities across a number of areas.
Writing prowess:
Generative AI improves writing quality and brand tone of voice, making it more challenging for consumers to spot scams. It also supports translation into multiple languages allowing fraudsters to target victims globally.
Technical breadth:
Fraudsters no longer need technical skills (html, JavaScript, and CSS) to create fake websites as there are fully productionized website cloning tools available. As the underlying capabilities behind AI technologies develop, we are also likely to see deepfake video and voice notes becoming mainstream fraud techniques.
Real-time responses:
Generative AI can respond in real-time to keep victims engaged, giving them little time to realize they are being scammed. And if a legitimate website changes, the cloned website can be replicated quickly.
Ease of integration:
Most top of funnel activities are fully automated, with human intervention not generally required. It is only when the victim has fallen for the scam that the human element is brought in to help carry it over the line. The result is that fraudsters no longer need to incur the costs (or would see a reduction in) and efforts associated with employing call center staff.
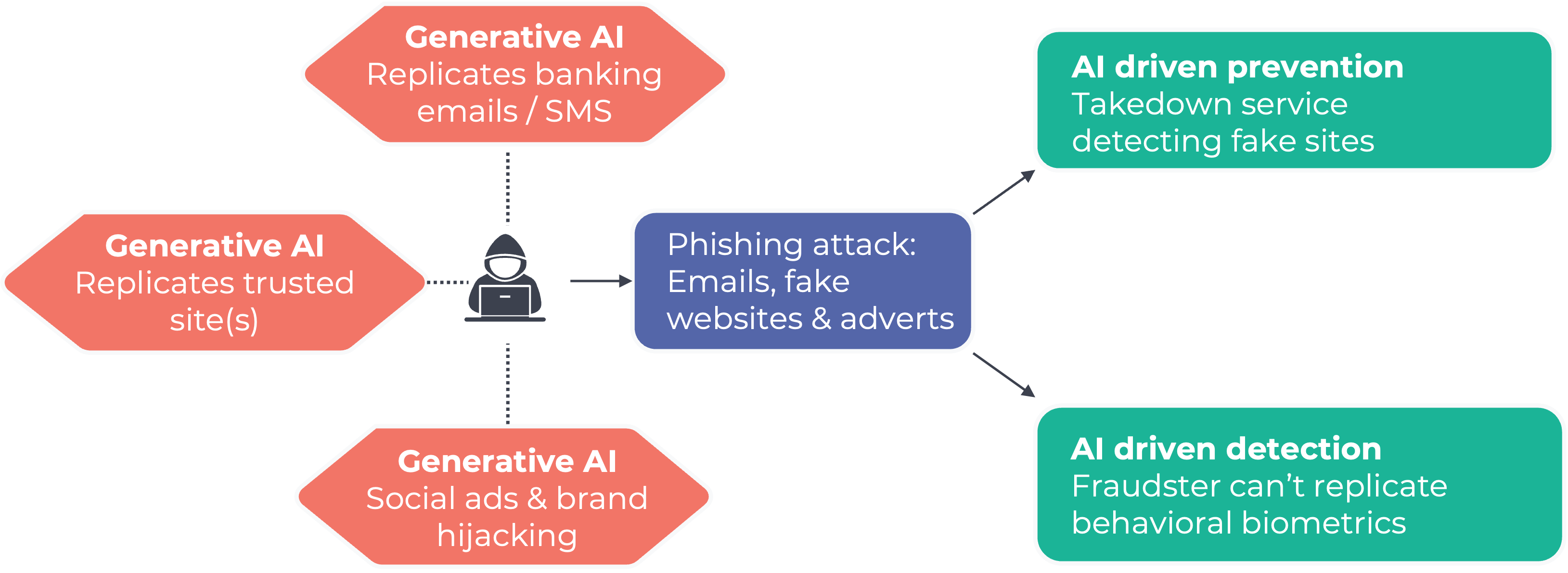
How to counter AI-driven phishing attacks
A decade ago, data breaches posed a significant problem for contact centers as fraudsters overwhelmed them with ATO (account takeover) attacks. The attack wasn’t necessarily sophisticated, but the volume meant that it became uneconomical for FI’s to use traditional ID&V techniques. To get the power back from the fraudsters, new techniques such as the introduction of voice biometrics and click to call became important capabilities in the organization's fraud tool kit.
Similar to the past, Generative AI is enabling criminals to exploit vulnerabilities in SMS OTP authentication. As the fraudsters enhance their toolkit, organizations need to simultaneously enhance their fraud prevention toolkit.
The fraud prevention toolkit
Recognize genuine users (and conversely when it is a fraudster)
- Behavioral biometrics: Recognize genuine users based on their behavior patterns and reduce reliance on traditional methods like SMS OTP and knowledge-based elements
- Cryptographic device binding: recognize and validate the device used for transactions
- Location analysis: Consistently analyze transaction locations for authenticity
Leverage signals from disparate sources
- Signal augmentation: Orchestrate signals gathered from both internal and external sources and enhance datasets with real-time intelligence to detect emerging threats more effectively
Implement dynamic user journeys
- Risk based authentication: Mitigate specific identified risk (e.g. behavioral analysis, biometric authentication) and location mismatch (e.g. scanning a QR code for physical presence assurance)
- Introduce dynamic fraud warnings & interventions for customers
Protect their brand
- Automated website takedowns: Reduce the time fraudulent sites remain online by automating takedown efforts
- Social media account protection
- Internal security: Ensure strong customer authentication is in place and staff go through regular phishing training
Behavioral biometrics and cryptographic device fingerprinting
Augmentation strategies that encompass behavioral biometrics and device recognition play a crucial role in reducing fraud risks by providing faster and more efficient results.
Device fingerprinting
Callsign’s layered device fingerprint approach uses proprietary algorithms based on both software and hardware attributes across hundreds of datapoints. Our device binding capability (where the device is “bound” to the user with a cryptographic key stored on the user’s device), delivers a strong attribute which is used in determining whether an interaction is legitimate or fraudulent and satisfies the possession requirements of PSD2’s SCA stipulations. It's also able to identify a device across browsers. You can read more about our capabilities here.
Behavioral biometrics
At Callsign we collect and analyze user interaction data that organizations can use to build individual user profiles that enable both specific user authentication and the identification of known fraud risks, reducing the reliance on traditional methods.
Our modelling approach looks for two things:
- 1:1 – comparing the transaction to a profile built for that specific user, with results packaged in a regulatory compliant manner under inherence
- 1:many – comparing the transaction to profiles of fraudulent MO’s developed across many events on the Callsign Network
This approach allows organizations to confidently authenticate users passively – reducing the reliance on OTP and knowledge factors, whilst also identifying known fraud risks that can be considered as part of an overall decision. In practical terms, this approach can reduce the need for SMS OTPs by over 40% while maintaining high acceptance rates and low false positives.
Through our powerful no-code Orchestration Layer, organizations can augment these insights with their own in-house data and third-party vendors to further reduce the risk exposure to phishing attacks and other fraud threats.
By adopting behavioral biometrics and orchestration tools, businesses can more accurately identify instances of fraud and dynamically adjust user journeys to prevent genuine transactions from being flagged incorrectly – improving the overall customer experience.
The rise of Generative AI may have ushered in a new era of cyber threats, particularly in the form of AI-driven phishing attacks but with the right tools and strategies, organizations can enhance their fraud prevention efforts and stay ahead of cybercriminals.




